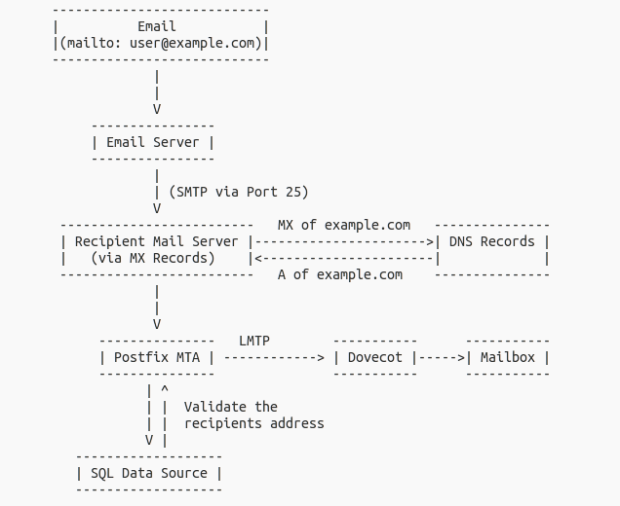
In the last blog post, we have set up the necessary tools for an email server to function and configured them. Now we need to test email delivery and check if the server is configured properly. So before we test, we also need to setup an email client. In this case we will use Roundcube as discussed in the previous post.
-
Roundcube
-
Configure Roundcube
Enable https: In /etc/apache2/sites-available/default-ssl.conf
SSLCertificateFile /etc/ssl/certs/mailserver.pem SSLCertificateKeyFile /etc/ssl/private/mailserver.key
To add Roundcube configuration to apache:
Include /etc/roundcube/apache.conf Alias / /var/lib/roundcube/
Reload apache:
service apache2 reload
Add default server:
vi /etc/roundcube/main.inc.php file and set:
$rcmail_config['default_host'] = 'localhost';
To permanently redirect http to https, in /etc/apache2/sites-available/000-default.conf add
Redirect permanent / https://youripaddress/
-
Configure plugins:
Config plugins in /etc/roundcube/main.inc.php
$rcmail_config['plugins'] = array( 'archive', 'managesieve', 'password', );
Set the password configuration. The password query is used when updating the password through roundcube, adjusting to the table structure by posty API.
$rcmail_config['password_minimum_length'] = 10; $rcmail_config['password_db_dsn'] = 'mysql://mailuser:mailuserpass@127.0.0.1/emailserver'; $rcmail_config['password_query'] = "UPDATE users_view SET password=ENCRYPT (%p, CONCAT('$6$', SUBSTRING(SHA(RAND()), -16))) WHERE email=%u";
-
-
Testing email delivery
Testing local mail delivery using mail command:
echo Hello | mail test@mailserverdemo.com
You can now log in with Roundcube and check if the mail is delivered.
You can also use telnet command to see if you can connect localhost using smtp.
telnet localhost smtp
Type ‘QUIT’ to exit
Test if you can connect to gmail:
telnet gmail-smtp-in.l.google.com. 25
Likewise, you can test email delivery using roundcube by sending an email to your gmail account and vise versa.
Note: You need to make sure your MX records are set up properly for email delivery outside your system. Usually port 25 will be blocked by your ISP so you may need to check your ports in case of non delivery
-
Web administration using Posty Web UI
Optionally you may want to use the posty API using a web UI. For this posty Web UI is also available from https://github.com/posty
Download and install posty Web UI
wget wget -o posty_webui.zip https://github.com/posty/posty_webui/archive/master.zip unzip posty_webui.zip cp -r posty_webui /var/lib/ cp posty_webui
Adjust the configurations according to your needs in the settings.json like url and api keys
vi settings.json
Add confuration for posty web app:
mkdir /etc/posty_webui vi /etc/posty_webui/apache.conf
Add the following and save:
Alias "/admin" "/var/lib/posty_webui" <Directory "/var/lib/posty_webui"> DirectoryIndex index.html Order allow,deny Allow from all AllowOverride All Require all granted </Directory>
Include the configuration in the main apache config:
vi /etc/apache2/sites-enabled/default-ssl.conf
Add the following after the line ‘Include /etc/phpmyadmin/apache.conf’
Include /etc/posty_webui/apache.conf
Secure your API web administration with an admin password:
Create your .htpasswd file using htpasswd command and file in the /etc/posty_webui/ directory
You need to make some changes to the posty REST server if you are going to enforce secure connection. Since your web UI is served as secure http, when calling the posty API without https, your browser will block these connections. For this reason, instead of webrick as the default server, we can use thin server instead which provides secure http. To enable https, just install thin server:
Change directory to your posty API folder:
cd /home/ubuntu/posty_api_master/
Add thin server to to the gem file.
vi Gemfile
Add the “gem ‘thin’, ‘~> 1.7.1′” to the list of gems, to install thin server:
gem 'rack', ... gem 'thin', '~> 1.7.1' gem 'grape', ...
Run bundle installer.
bundle install
Testing thin server:
thin –help should give you a list of options to start the thin server.
Run thin server with SSL enabled. You need to provide the signed certificate and key for using SSL:
thin --ssl --ssl-key-file /etc/ssl/private/mailserver.pem --ssl-cert-file /etc/ssl/certs/mailserver.pem
Configure your port, eg running on port 9292 with SSL:
thin -p 9292 --ssl --ssl-key-file /etc/ssl/private/mailserver.pem --ssl-cert-file /etc/ssl/certs/mailserver.pem start
You should see the console that looks like this:
... Using rack adapter Thin web server (v1.7.1 codename Muffin Mode) Maximum connections set to 1024 Listening on 0.0.0.0:9292, CTRL+C to stop ...
To run as a daemon sersvice:
thin -d -p 9292 --ssl --ssl-key-file /etc/ssl/private/mailserver.pem --ssl-cert-file /etc/ssl/certs/mailserver.pem start
Now you can login to your admin site in https://youripaddress/admin
-
Add spam prevention:
You can prevent a lot of spam by tightening incoming traffic to postfix and using RBL List for spam ip blacklists. Just add the following to /etc/postfix/main.cf. You may need add/remove parameters and adjust according to your needs:
disable_vrfy_command = yes smtpd_delay_reject = yes smtpd_helo_required = yes smtpd_helo_restrictions = permit_mynetworks, reject_non_fqdn_hostname, reject_invalid_hostname smtpd_recipient_restrictions = permit_mynetworks, permit_sasl_authenticated, reject_non_fqdn_hostname, reject_non_fqdn_sender, reject_non_fqdn_recipient, reject_unauth_destination, reject_unauth_pipelining, reject_invalid_hostname reject_rbl_client bl.spamcop.net, reject_rbl_client cbl.abuseat.org, reject_rbl_client dnsbl.sorbs.net, reject_rbl_client zen.spamhaus.org smtpd_error_sleep_time = 1s smtpd_soft_error_limit = 10 smtpd_hard_error_limit = 20
-
Mail statistics using mail graph
Mailgraph is a very useful tool for giving statistics of your email server, i.e it gives you the number of emails accepted or rejected and their average for a range like day, week, month and year.
Installation is simple and straight forward. You need to also install rrd tool, a graph tool for using mailgraph. Install them using the following command:
sudo apt-get install rrdtool mailgraph
To configure mailgraph, you can use the following command:
dpkg-reconfigure mailgraph
Now we want to mailgraph to be accesible from your browser to see the statistics, so create a directory called ‘mailgraph’ inside your web server’s public directory and copy mailgraph from its location to the directory.
mkdir /var/www/html/mailgraph cp -p /usr/lib/cgi-bin/mailgraph.cgi /var/www/html/mailgraph
Add site configuration for mailgraph
Alias "/mailgraph" "/var/www/html/mailgraph" <Directory /var/www/html/mailgraph/> AddHandler cgi-script .cgi .pl Options +ExecCGI Order allow,deny Allow from all AllowOverride All Require all granted </Directory>Add mailgraph to be served by apache server. In the apache configuration add the following:
Include /etc/phpmyadmin/apache.conf Include /etc/posty_webui/apache.conf Include /etc/mailgraph/apache.conf Include /etc/roundcube/apache.conf Alias / /var/lib/roundcube/
Point you web browser to https://yourwebsiteaddress/mailgraph/mailgraph.cgi, to see the statistics:
-
Logging:
For trouble shooting, you can check your logs for errors. Depending on the distribution, the locations may be different. In our case, the following are the log locations for emails, roundcube and apache server.
/var/log/syslog /var/log/mail.err /var/log/mail.log /var/log/roundcube/errors /var/log/apache2/error.log